MORIVPN
Encryption for your anonymity
The first service that combines VPN and TOR in one application and doesn't collect your data. Full control over your connection without restrictions or third-party infrastructure.



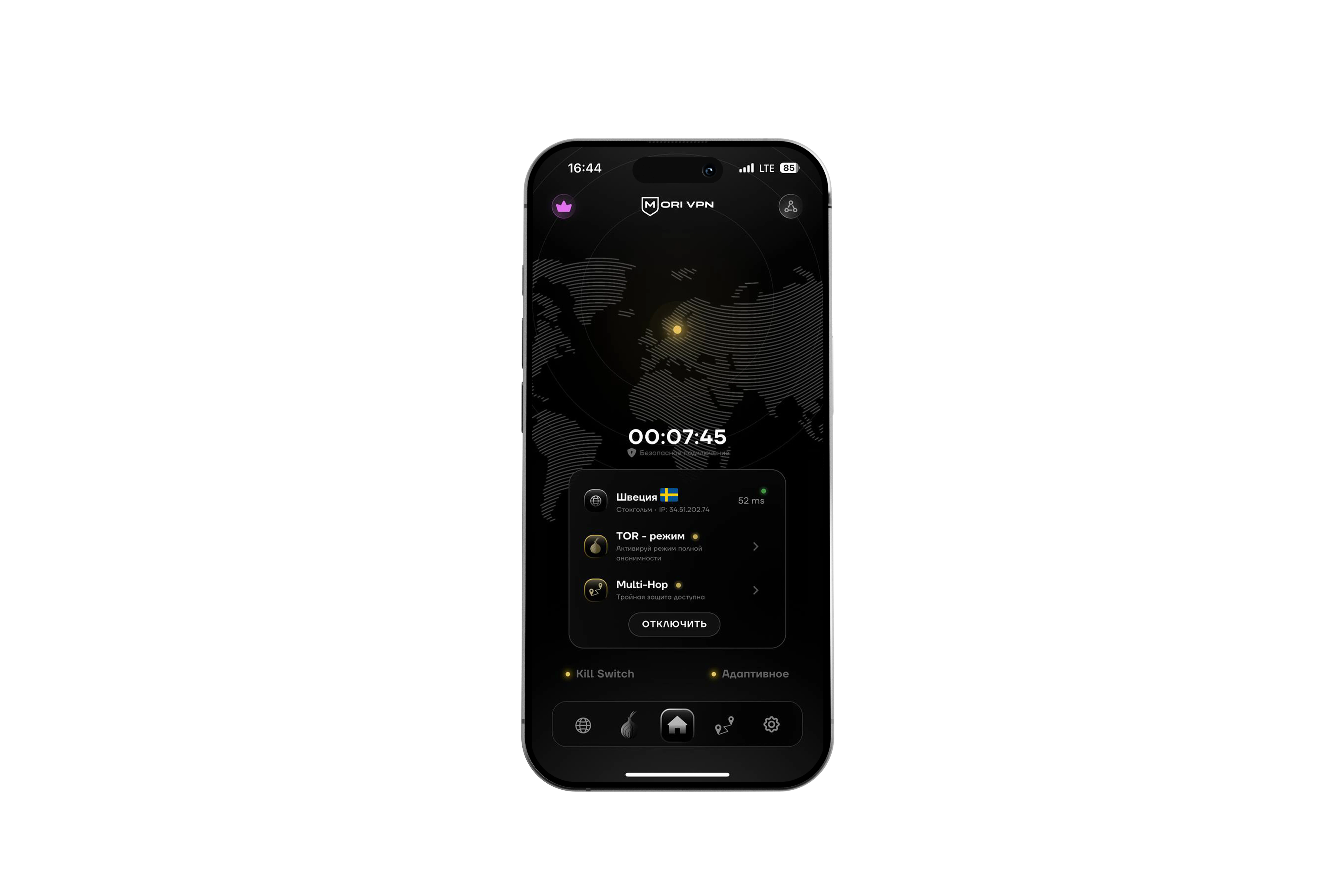
The first service that combines VPN and TOR in one application and doesn't collect your data. Full control over your connection without restrictions or third-party infrastructure.










Anonymous access without account
Email / Phone / KYC
No app-level identification
Device ID, UUID, App identifiers
No telemetry or App analytics
Crash logs, Usage stats, Diagnostics
No account-traffic link
Architecturally
Zero-Knowledge architecture
Service doesn't know who the traffic belongs to
Comparison based on public privacy policies and application architecture of services.
Proprietary bypass system. Not a standard VPN protocol.
Works with DPI and signature filtering

No manual configuration required

Proprietary bypass system

Adapts to new restrictions automatically

Provides stable access to all resources

Real cases representing the industry


Investigators had VPN IP and activity time from a website.
PureVPN provided on request who was connected to the server at that moment and from which real IP.
IP was matched with the provider.
Person was arrested.


By court order, the service handed over account authorization logs.
This was enough to link the account, IP, and real person.
Arrest.
We don't have the attack surface for deanonymization
It's impossible to log a specific user because the user as an entity doesn't exist.
No logs. No accounts. No metadata.




Do you use RAM-only servers?
Yes. Server infrastructure is configured so that data is not stored on persistent media. When the server restarts, information completely disappears.
Do you use your own DNS?
Yes. MORI VPN uses its own DNS or secure DoH/DoT channels. Third-party DNS providers and analytics services are not used.
Is there DPI, MITM, or traffic inspection?
No. We don't use DPI, don't analyze packets, and don't perform MITM interception. Traffic is transmitted encrypted without content inspection.
Can I use MORI VPN for P2P and torrent traffic?
Yes. MORI VPN doesn't restrict traffic types and doesn't apply filtering or connection prioritization.
How does TOR mode work in MORI VPN?
TOR-over-VPN mode is used. Traffic first passes through MORI VPN, then is routed through the TOR network. ISP and websites don't see TOR usage, TOR nodes don't see the real IP.
How much slower is TOR mode compared to regular VPN?
Significantly slower. Speed in TOR mode is limited by the TOR network itself and multi-node routing. This mode is designed for anonymity, not high speed.
Are there traffic or time limits?
No. There are no limits on traffic volume or usage time.
What happens when the VPN connection drops?
If you activated Kill Switch - the network is blocked until the secure connection is restored.